NIST SP 800-82r2 is a guide to securing industrial control systems (ICS). It provides an overview of ICS, identifies typical threats and vulnerabilities, and recommends security countermeasures. The guide is intended for a wide audience, including system owners, operators, and security professionals.

Key Takeaways:
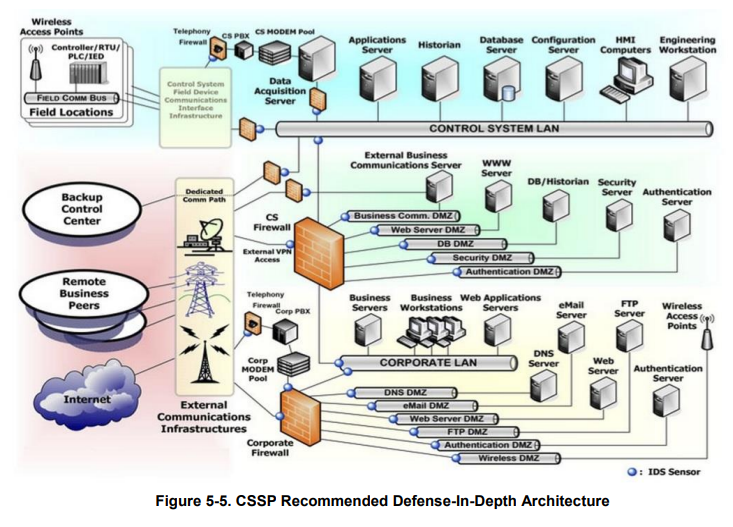
- ICS are critical infrastructure systems that control physical processes. In theory, they are supposed to be air-gapped for greater security, but they are often partially or heavily connected to the internet for updates or to facilitate remote or geographically dispersed ways of working. This in turn makes them vulnerable to cyberattacks.
- The most common threats to ICS include:
- Malware
- Phishing
- Denial-of-service attacks
- Physical attacks
- To protect ICS, it is important to implement a layered security approach that includes:
- Physical security
- Network security
- Device security
- Application security
- Human factors security
- NIST SP 800-82r2 provides detailed guidance on each of these security areas.
Comparison to Other NIST Publications:
NIST SP 800-82r2 is one of several NIST publications that address ICS security. Other relevant publications include:
- NIST SP 800-53: Security and Privacy Controls for Information Systems and Organizations
- NIST SP 800-83: Guide to Securing Control Systems
- NIST SP 800-94: Guide to Industrial Control Systems (ICS) Security for Small and Medium Organizations
NIST SP 800-82r2 is more specific than the other publications, as it focuses on the unique security challenges of ICS. It is also more comprehensive, as it provides detailed guidance on all aspects of ICS security.
Limitations or Drawbacks:
NIST SP 800-82r2 is a valuable resource for securing ICS, but it has some limitations. For example, the guide was published in 2015 so it provides a more conceptual or theoretical background rather than a direct lens on the latest threats and vulnerabilities. Additionally, parts of the guide can be quite technical and may be difficult to understand for non-technical audiences.
List of Major Sections:
- Introduction
- Overview of ICS
- Risk Management and Assessment
- Security Program Development and Deployment
- Architecture
- Applying Controls
- Appendices
ICS Overlay and Why it is Useful:
The ICS Overlay in Appendix G is based on the NIST 800-53 security controls. These controls are designed to protect information systems from a variety of threats. It maps the NIST 800-53 controls to the different components of an ICS system. This makes it easy to see which controls are relevant to a particular ICS system. By using the overlay, system owners and operators can identify specfici focus areas and vulnerabilities and take steps to mitigate them.
Other general uses include:
- To aid design of a new ICS system
- To assess the security of an existing ICS system
- To plan for security updates and patches
- To train security personnel on ICS security
Conclusion:
NIST SP 800-82r2 is a valuable resource for securing industrial control systems. It provides a comprehensive overview of ICS security and recommends specific security countermeasures. The guide is intended for a wide audience, including system owners, operators, and security professionals.
It can be a bit technical, but it provides a great overview for someone needing to get familiar with this area or wanting to use it to deepen their overall knowledge.
If you have any questions about NIST SP 800-82r2, please feel free to leave a comment below.